Bridging
Bridges are essential for cross-chain interoperability, allowing users and applications to transfer assets and messages between Ethereum and Taiko Alethia. However, cross-chain messaging and asset transfers introduce potential security risks. Taiko Alethia implements a secure bridge design leveraging Ethereum-equivalence, Merkle proofs, and the Signal Service smart contract.
This page explains how Taiko’s bridge works and answers key questions:
- How does the Taiko Alethia protocol enable secure cross-chain messaging?
- What is the Taiko Signal Service?
- How does Taiko Alethia’s bridge implementation work?
Cross-chain messaging
Section titled “Cross-chain messaging”Taiko Alethia uses a trust-minimized, Ethereum-equivalent design for secure cross-chain messaging. This is achieved by synchronizing world state roots between L1 (Ethereum) and L2 (Taiko) and using Merkle proofs for verification.
Storing block hashes across chains
Section titled “Storing block hashes across chains”Two smart contracts are responsible for maintaining cross-chain state:
- TaikoInbox (deployed on Ethereum) → Stores L2 world state roots
- TaikoAnchor (deployed on Taiko) → Stores L1 world state roots
Whenever an L2 block is created, the corresponding world state root of the enclosing Ethereum L1 block is stored in the TaikoAnchor contract using the anchor transaction. This ensures that only valid state transitions are recognized.
Similarly, the L2 world state root is stored in TaikoInbox using the syncChainData function.
Verifying values across chains using Merkle proofs
Section titled “Verifying values across chains using Merkle proofs”A Merkle tree is a data structure that enables efficient verification of whether a specific value exists within a dataset without requiring full access to all data. The Merkle tree consists of:
- Merkle root: A cryptographic fingerprint representing the entire dataset.
- Merkle proof: A series of intermediate hashes that allow recomputing the Merkle root.
- Leaf node: The actual value being verified.
- Sibling hashes: A list of intermediate hashes required to reconstruct the Merkle root.
By leveraging Merkle trees, Taiko Alethia ensures that messages and transactions sent on one chain can be securely validated on the other. Sibling hashes play a critical role in this process, as they provide the necessary path for recomputing the Merkle root efficiently.
The Signal Service
Section titled “The Signal Service”The Signal Service is a core component enabling decentralized and secure messaging. It is deployed on both L1 and L2, allowing any contract or user to send and verify messages.
Key functions
Section titled “Key functions”sendSignal(message): Stores a message in the Signal Service contract.verifySignalReceived(message, proof): Checks if a message was sent on the source chain using a Merkle proof.
Verification process
Section titled “Verification process”- The sender calls
sendSignal(message)on the source chain. - The recipient retrieves the Merkle proof of the message using
eth_getProof. - The proof is submitted to
verifySignalReceivedon the destination chain. - The contract reconstructs the Merkle root using sibling hashes and verifies it against stored state roots.
- If the proof is valid, the message is considered received.
How the bridge works
Section titled “How the bridge works”The bridge allows trust-minimized asset transfers between Ethereum and Taiko. It leverages the Signal Service for security, ensuring assets are transferred only if the source chain transaction is verifiable.
Flow of an asset transfer
Section titled “Flow of an asset transfer”Sending assets from source chain
Section titled “Sending assets from source chain”When a user initiates a transfer:
- The user sends assets (ETH or ERC tokens) to the Bridge contract.
- The Bridge contract:
- Locks the ETH/ERC token.
- Calls
sendSignal(message)on the Signal Service.
- The signal is stored on the source chain.
Diagram: Sending a message on the source chain
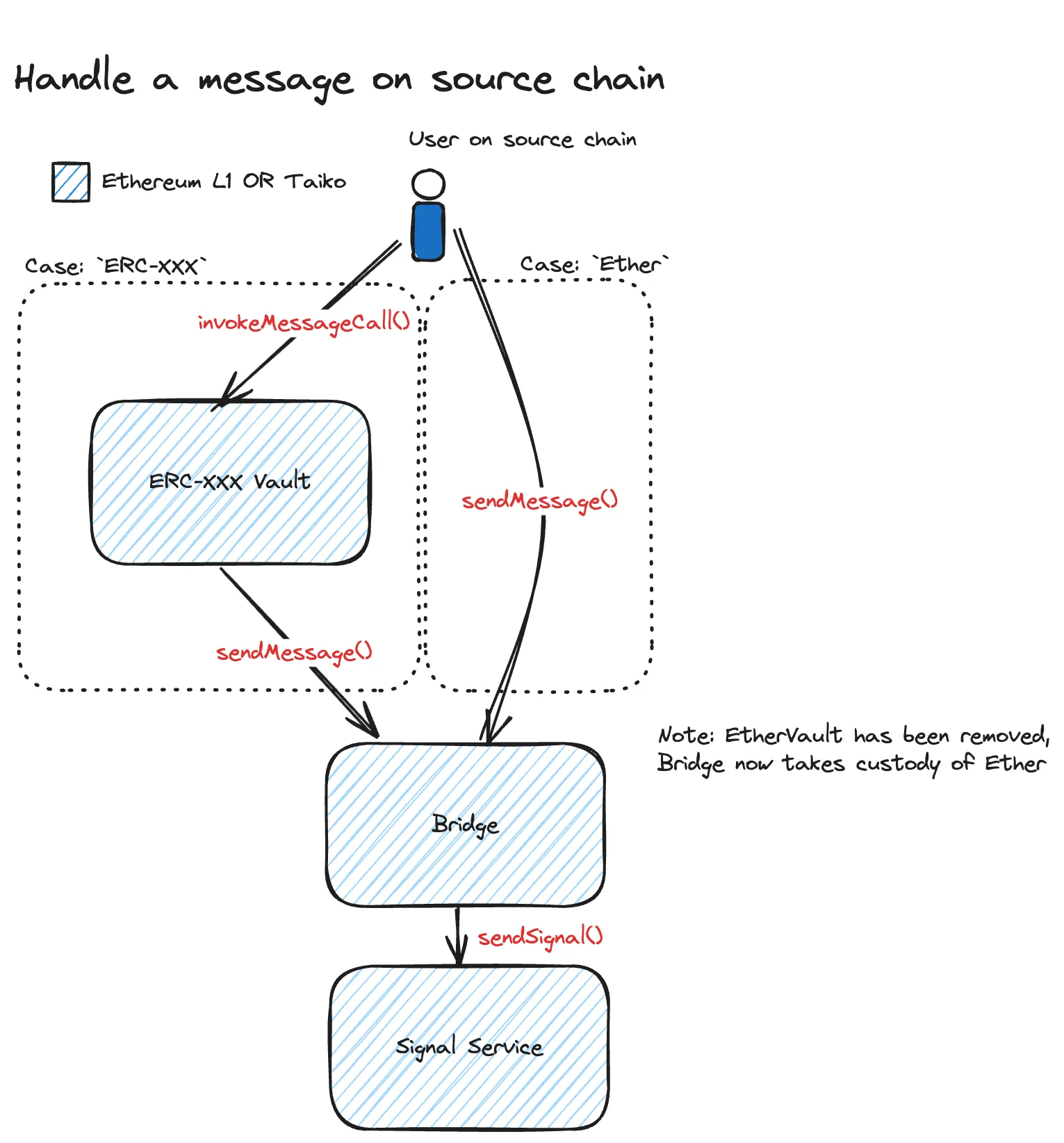
Receiving assets on destination chain
Section titled “Receiving assets on destination chain”To complete the transfer:
- A relayer (or user) submits a Merkle proof from the source chain.
- The Bridge contract verifies the proof using the Signal Service.
- If valid:
- ETH/ERC tokens are released to the recipient.
- The transfer is marked as complete.
Diagram: Processing a message on the destination chain
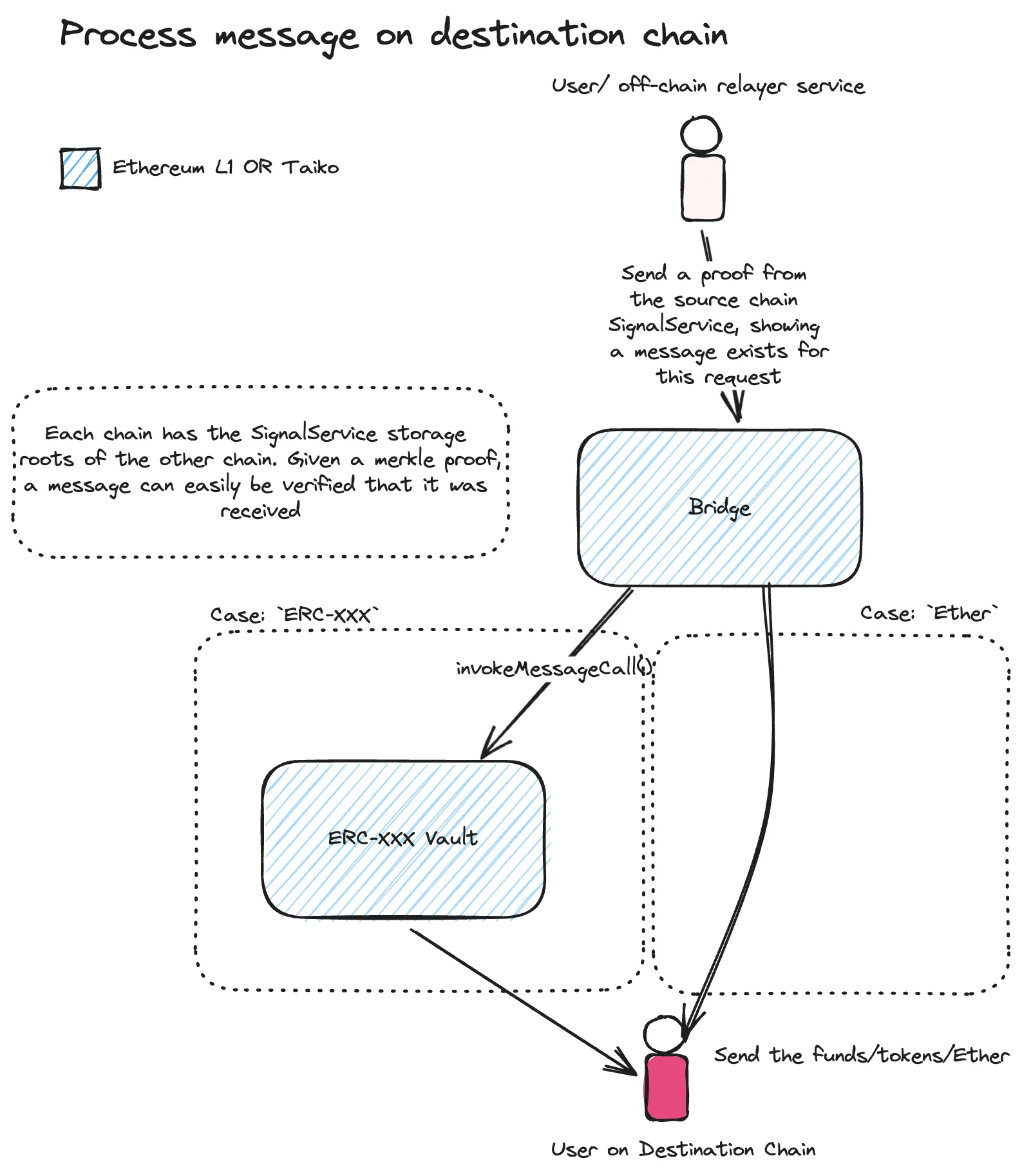
Ether bridging
Section titled “Ether bridging”Taiko Alethia’s bridge supports Ether transfers in two cases:
- Direct ETH transfer: The user calls
sendMessageon the Bridge contract. - ETH + ERC token transfer: The user calls
sendTokenon the appropriate token vault (ERC20Vault,ERC721Vault, orERC1155Vault), including ETH as part of the transaction.
ERC-20, ERC-721, and ERC-1155 token bridging
Section titled “ERC-20, ERC-721, and ERC-1155 token bridging”Token bridging requires a BridgedERC contract on the destination chain.
Bridging ERC tokens to the destination chain
Section titled “Bridging ERC tokens to the destination chain”- The ERC token contract must exist on the destination chain.
- The sender calls
sendTokenon the appropriate token vault (ERC20Vault,ERC721Vault, orERC1155Vault) on the source chain. - The vault transfers the token to the Bridge contract and generates a Merkle proof.
- The recipient submits a Merkle proof on the destination chain.
- If valid, the BridgedERC contract mints the corresponding amount.
Bridging back to the canonical chain
Section titled “Bridging back to the canonical chain”- The sender calls
sendTokenon theBridgedERCcontract (destination chain). - The contract burns the token and generates a Merkle proof.
- The recipient submits the proof on the canonical chain.
- The canonical TokenVault contract releases the original token.
Summary
Section titled “Summary”| Feature | Taiko Alethia Bridge |
|---|---|
| Security Model | Merkle proofs + world state root sync |
| Asset Types | ETH, ERC-20, ERC-721, ERC-1155 |
| Validation | On-chain proof verification |
| Permissionless | No centralized operators |
| Trust-Minimized | No third-party reliance |
The Taiko Alethia bridge is a fully decentralized, secure, and Ethereum-equivalent solution for cross-chain asset transfers. Developers can use its Signal Service for their own bridging implementations.